How often should I conduct a cybersecurity risk assessment?
In an era where cybersecurity threats are increasingly sophisticated, regular risk assessments are crucial to safeguarding sensitive business data. Conducting these assessments helps identify vulnerabilities and strengthens your defenses, but determining the frequency can be challenging. Here, we’ll dive into the factors influencing cybersecurity risk assessment timing and offer guidance on how often your business should undertake these crucial evaluations.
Understanding Cybersecurity Risk Assessments
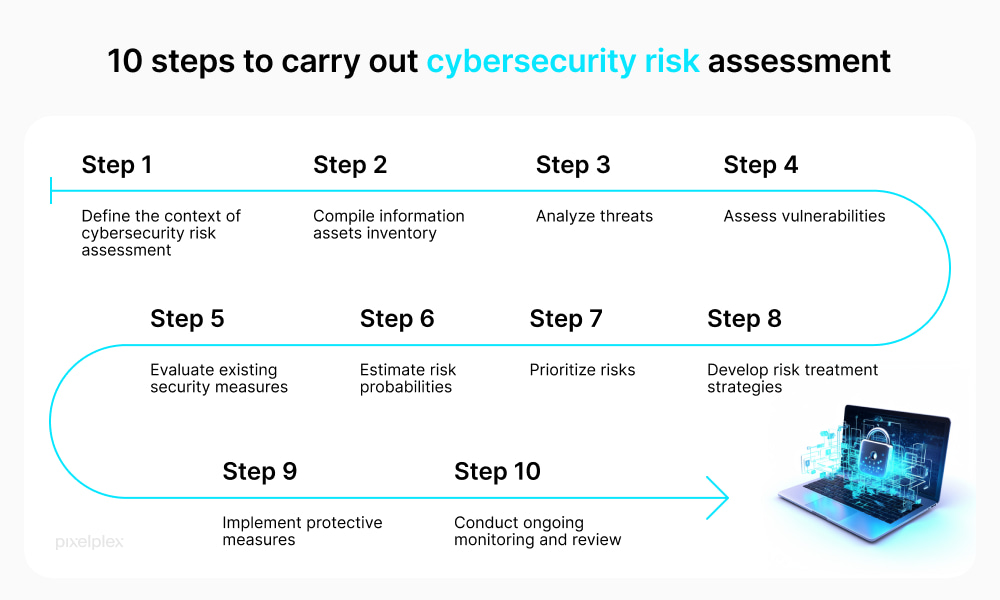
A cybersecurity risk assessment systematically identifies, evaluates, and addresses potential vulnerabilities within your IT environment. These assessments help gauge your current security posture, uncover gaps, and prioritize areas for improvement. Typically, an assessment includes a review of:
- Digital assets: Systems, data, and applications
- Threat landscape: Potential threats relevant to your business
- Vulnerabilities: Weak points within the IT environment
- Likelihood and impact: Chances of an attack and its potential damage
- Mitigation strategies: Actions to address risks
Regularly assessing these elements ensures your defenses are up to date and can adapt to evolving threats.
Recommended Frequency for Cybersecurity Risk Assessments
While there’s no one-size-fits-all answer, businesses should generally conduct cybersecurity risk assessments at least once a year. However, several factors may warrant more frequent evaluations.
1. Regulatory and Compliance Requirements
Businesses in regulated industries, like healthcare and finance, often face stringent compliance standards that specify assessment frequency. For example, the Health Insurance Portability and Accountability Act (HIPAA) mandates regular assessments for healthcare entities, while the Payment Card Industry Data Security Standard (PCI DSS) requires assessments for businesses handling credit card data. These requirements typically call for annual or even semi-annual evaluations to ensure data security and regulatory compliance.
2. Changes in IT Infrastructure or Business Operations
Significant changes in your technology stack, such as implementing new software, adding hardware, or migrating data to the cloud, can create new vulnerabilities. Likewise, mergers, acquisitions, and business expansions may increase risk exposure. Each time you modify your IT infrastructure, consider conducting a risk assessment to identify and address any new vulnerabilities.
3. Response to Cybersecurity Incidents or Threats
If your business has experienced a security breach, malware attack, or other cyber incident, a risk assessment can help you understand how the event occurred, identify weaknesses, and develop strategies to prevent future incidents. Even if an attack was unsuccessful, new threats often highlight gaps that should be addressed.
4. Introduction of New Compliance Standards
With the evolving regulatory landscape, new cybersecurity standards and frameworks are introduced regularly. When compliance requirements change or new industry guidelines emerge, it’s wise to perform an updated assessment. Staying proactive ensures that your business remains compliant and avoids potential fines or legal issues.
5. Annual Assessments as a Minimum Standard
Even in the absence of major changes, annual assessments are considered a minimum best practice for businesses of all sizes. This practice keeps your cybersecurity program current, as the annual cycle allows you to address typical vulnerabilities, like outdated software, weak passwords, and unsecured networks, before they become critical.
Types of Cybersecurity Risk Assessments
To determine how often you should assess risks, it’s helpful to understand the different types of cybersecurity assessments:
- Internal assessments: Focus on identifying vulnerabilities within your internal network, such as access controls, employee practices, and software updates.
- External assessments: Examine external threats, including potential cyberattacks on public-facing systems like websites or cloud services.
- Compliance assessments: Ensure that your cybersecurity measures align with industry regulations and standards.
- Penetration testing: Involves simulating an attack to uncover vulnerabilities, particularly valuable when significant changes occur.
The frequency for each type may vary based on your business needs, industry, and regulatory obligations.
Developing a Proactive Assessment Schedule
Creating a proactive assessment schedule helps keep your business secure without disruption. Here are a few key strategies to consider:
- Monthly Vulnerability Scans: Regular scans allow for the quick detection of potential security weaknesses in your systems. Monthly scans provide ongoing insights, enabling faster responses to emerging threats.
- Quarterly Internal Audits: Conducting internal audits on a quarterly basis helps identify and resolve issues that may have been missed. These audits should review access controls, user permissions, and any changes in internal processes.
- Bi-Annual or Annual Penetration Tests: Penetration testing twice a year, or at least annually, can help uncover vulnerabilities that attackers might exploit.
- Annual Full-Scale Assessments: A thorough, comprehensive assessment annually ensures that every aspect of your cybersecurity posture is reviewed.
Key Benefits of Regular Cybersecurity Risk Assessments
Conducting regular cybersecurity risk assessments offers numerous advantages that go beyond regulatory compliance:
- Early Threat Detection: Regular assessments reveal vulnerabilities before they’re exploited, helping you implement timely countermeasures.
- Enhanced Incident Response: By identifying gaps in your security strategy, assessments strengthen your incident response plan.
- Cost Savings: Preventative security measures reduce the likelihood of costly breaches and operational disruptions.
- Reputational Protection: Consistently securing your data builds trust with clients, partners, and stakeholders.
Tailoring Assessment Frequency to Business Needs
Ultimately, the frequency of cybersecurity risk assessments should align with your business’s specific needs. Smaller businesses may opt for annual assessments, while larger enterprises might benefit from quarterly or bi-annual evaluations. The key is to create a flexible, proactive schedule that aligns with your industry, compliance needs, and operational changes.
Conclusion
Maintaining a secure IT environment is an ongoing process that requires regular attention. By scheduling cybersecurity risk assessments according to your business’s unique needs, you can safeguard against potential threats and adapt to the ever-evolving threat landscape. Whether prompted by regulatory demands, system changes, or an annual routine, consistent risk assessments ensure your organization remains secure, compliant, and resilient.

