How can Endpoint Encryption Solutions Enhance Data Security?
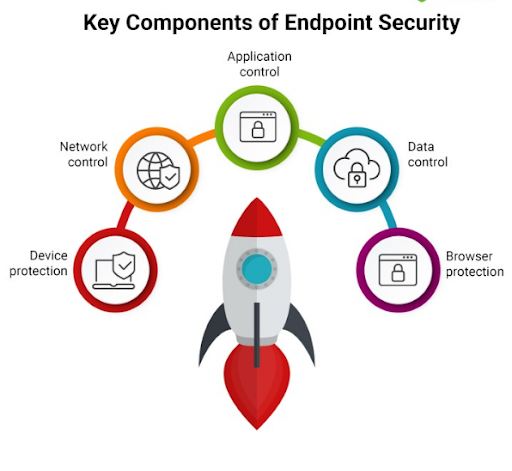
In today’s interconnected world, data security is paramount for businesses of all sizes. As cyber threats continue to evolve and become more sophisticated, protecting sensitive information from unauthorized access and breaches is a top priority. Endpoint encryption solutions offer a powerful defense against data breaches by encrypting data at the endpoint, ensuring that even if a device is lost, stolen, or compromised, the data remains secure. In this blog, we’ll explore the importance of endpoint encryption and how Aileron IT, the leading Managed Service Provider (MSP) in western Wisconsin, can help businesses enhance their data security with advanced endpoint encryption solutions.
Understanding Endpoint Encryption
Endpoint encryption is a security measure that involves encrypting data stored on endpoint devices such as laptops, desktops, smartphones, and tablets. By encrypting data at the endpoint, businesses can protect sensitive information from unauthorized access, even if the device falls into the wrong hands.
The Importance of Endpoint Encryption
- Protection Against Data Breaches: Data breaches can have devastating consequences for businesses, including financial losses, damage to reputation, and legal liabilities. Endpoint encryption helps mitigate the risk of data breaches by rendering stolen or lost devices unusable to unauthorized users.
- Compliance Requirements: Many industries are subject to strict regulatory requirements regarding the protection of sensitive data. Endpoint encryption solutions help businesses achieve compliance with regulations such as HIPAA, GDPR, and PCI DSS by ensuring that sensitive data is encrypted and protected at all times.
- Securing Remote Workforce: With the rise of remote work, securing endpoint devices has become more challenging than ever. Endpoint encryption solutions provide an extra layer of security for remote workforce environments, ensuring that sensitive data remains protected, regardless of where employees are working from.
- Preventing Data Loss: In addition to protecting against external threats, endpoint encryption also helps prevent data loss due to accidental or intentional actions by employees. By encrypting data at the endpoint, businesses can maintain control over their sensitive information and prevent unauthorized access.
How Aileron IT Can Help
- Tailored Endpoint Encryption Solutions: At Aileron IT, we understand that every business has unique data security requirements. That’s why we offer tailored endpoint encryption solutions designed to meet the specific needs and challenges of your organization. Whether you’re a small business or a large enterprise, we have the expertise and experience to implement the right endpoint encryption solution for your business.
- Comprehensive Security Assessment: Our team conducts a thorough security assessment to identify potential vulnerabilities in your existing IT infrastructure. Based on our findings, we recommend the most appropriate endpoint encryption solution to strengthen your data security posture and protect your sensitive information.
- Implementation and Deployment: We handle all aspects of implementation and deployment, ensuring a seamless integration with your existing IT systems and minimal disruption to your business operations. Our experienced technicians work efficiently to deploy endpoint encryption solutions quickly and effectively, so you can start benefiting from enhanced data security right away.
- Ongoing Monitoring and Support: Our commitment to your security doesn’t end with implementation. We provide ongoing monitoring and support to ensure that your endpoint encryption solution remains effective and up-to-date. Our team monitors for any security incidents or anomalies, promptly addressing any issues that may arise to maintain the integrity of your data security.
Common Challenges and Concerns with Endpoint Encryption
While endpoint encryption offers numerous benefits for enhancing data security, businesses may encounter some challenges and concerns when implementing these solutions. Here are some common issues to consider:
- Performance Impact: Some businesses may be concerned about the potential performance impact of endpoint encryption on their devices. While encryption processes can consume additional resources, advancements in encryption technology have minimized performance overhead, ensuring that encryption does not significantly impact device performance.
- User Experience: Another concern is the impact of endpoint encryption on the user experience. Businesses may worry that encryption processes could slow down device boot times or hinder user productivity. However, with properly configured encryption solutions and user training, businesses can minimize disruptions to the user experience and ensure seamless operation.
- Key Management: Effective key management is essential for ensuring the security of encrypted data. Businesses must establish robust key management practices to securely generate, store, and distribute encryption keys. Failure to properly manage encryption keys could result in data loss or unauthorized access to sensitive information.
- Compatibility and Integration: Businesses may face compatibility issues when integrating endpoint encryption solutions with existing IT systems and software applications. It’s crucial to choose encryption solutions that are compatible with your organization’s infrastructure and can seamlessly integrate with your existing workflows to ensure smooth operation.
How Aileron IT Addresses These Challenges
- Performance Optimization: At Aileron IT, we understand the importance of balancing data security with performance. Our team works closely with clients to implement endpoint encryption solutions that minimize performance impact while maximizing data protection. We leverage advanced encryption technologies and optimization techniques to ensure that encryption processes run efficiently without compromising device performance.
- User Training and Support: We provide comprehensive user training and support to help businesses navigate the implementation of endpoint encryption solutions. Our experienced technicians offer guidance on best practices for using encrypted devices and address any user concerns or issues to ensure a positive user experience.
- Robust Key Management: We help businesses establish robust key management practices to ensure the security of encrypted data. Our team assists with key generation, storage, and distribution, implementing industry best practices to safeguard encryption keys and prevent unauthorized access to sensitive information.
- Compatibility Testing and Integration: Before deploying endpoint encryption solutions, we conduct thorough compatibility testing to ensure seamless integration with our clients’ existing IT systems and software applications. Our technicians work closely with clients to address any compatibility issues and implement solutions that align with their specific needs and requirements.
By addressing these common challenges and concerns with endpoint encryption, Aileron IT helps businesses overcome obstacles and maximize the benefits of data security solutions.
Conclusion
In conclusion, endpoint encryption solutions play a crucial role in enhancing data security and protecting sensitive information from unauthorized access and breaches. With Aileron IT as your trusted IT partner, you can benefit from advanced endpoint encryption solutions tailored to your business’s unique needs and challenges. Contact us today to learn more about how we can help you enhance your data security with endpoint encryption. Let us help you safeguard your business against cyber threats with advanced endpoint encryption solutions!

