What are the best practices for creating strong passwords and managing them securely?
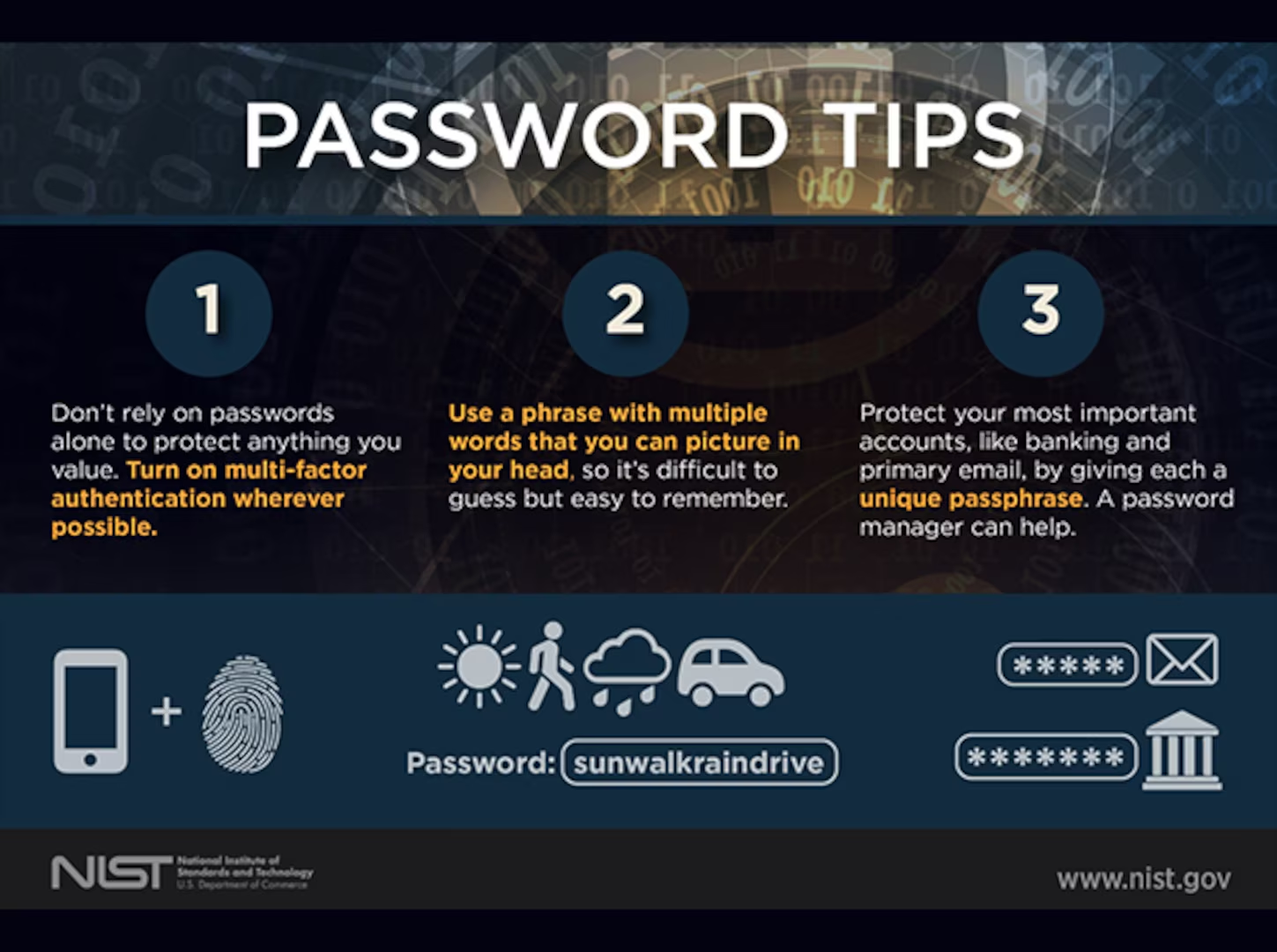
In today’s digital world, the strength of your passwords can make the difference between a secure online experience and a security breach. Strong passwords and smart management are crucial for protecting sensitive information, whether for business or personal use. However, many users still rely on weak passwords or poor management practices that leave their accounts vulnerable. This guide outlines best practices for creating strong passwords, storing them securely, and maintaining good password hygiene.
1. Characteristics of a Strong Password
Creating a secure password starts with understanding the essential elements that make it difficult to crack.
Length Matters:
Aim for passwords that are at least 12-16 characters long. Longer passwords are exponentially more difficult for hackers to crack, even with sophisticated software.
Use a Mix of Characters:
Strong passwords include a combination of uppercase and lowercase letters, numbers, and special symbols (e.g., !, #, %, &). This variety adds complexity, making the password harder to guess.
Avoid Common Words and Phrases:
Avoid dictionary words, names, or popular phrases. Hackers often use automated programs that can quickly test these combinations. Instead, try unique, unrelated words combined in a way that only makes sense to you.
Use a Passphrase:
Creating a passphrase—a series of random words strung together—can help ensure both strength and memorability. A phrase like “YellowHorse!Lake42%Tulip” is difficult to guess yet memorable.
Avoid Personal Information:
Steer clear of using easily accessible personal details such as your name, birthday, or common hobbies. Cybercriminals often look for this information on social media to make educated guesses.
2. Best Practices for Password Creation
Substitute Characters and Add Symbols:
Incorporating symbols and numbers creatively (e.g., “P@ssw0rd!”) strengthens passwords. Avoid predictable substitutions, though; instead of replacing “a” with “@” in every case, mix it up to make the password less guessable.
Avoid Sequential or Repetitive Patterns:
Patterns like “1234” or “abcd” are some of the first combinations hackers will try. Similarly, avoid repeated characters like “aaaa” or “1111” as they’re easy for attackers to crack.
Change Default Passwords:
Devices or online services often come with default passwords, which are often easy to guess. Always change these defaults to unique passwords upon setup.
Avoid Reusing Passwords Across Accounts:
Reusing passwords increases vulnerability. If a hacker gains access to one account, they can easily access others with the same password. Creating unique passwords for each account greatly reduces this risk.
3. Managing Passwords Securely
Strong passwords are only as safe as the methods you use to manage them. Here are strategies to keep passwords secure and organized:
1. Use a Password Manager
A reputable password manager can securely store and organize passwords, eliminating the need to remember multiple complex combinations. Password managers encrypt your passwords and require only one master password for access, streamlining login while boosting security.
2. Enable Two-Factor Authentication (2FA)
Whenever available, activate two-factor authentication on your accounts. 2FA requires an additional step—like entering a code sent to your phone—when logging in, adding an extra layer of security.
3. Avoid Writing Passwords Down
Writing passwords on paper or saving them in unencrypted files can be risky, as physical notes or plain text files can easily fall into the wrong hands. If you must write them down, secure the notes in a safe, inaccessible location.
4. Don’t Share Passwords
Sharing passwords, even with people you trust, increases risk. If they lose the information or it ends up in the wrong hands, your account becomes vulnerable. If collaboration is necessary, use secure sharing methods offered by password managers.
5. Regularly Update Passwords
Changing passwords every few months can help keep accounts secure. Make this especially frequent for high-value accounts (e.g., banking or business accounts) or if you suspect a breach has occurred.
4. Understanding Common Threats and How to Avoid Them
Cybercriminals use various techniques to crack passwords. Awareness of these methods can help you avoid common pitfalls.
Phishing Attacks:
Phishing is a social engineering tactic where attackers send fraudulent messages, often via email, to trick users into revealing their passwords. Always verify the sender’s authenticity and avoid clicking suspicious links.
Credential Stuffing:
This technique involves attackers using credentials from previous data breaches to gain access to multiple accounts. Unique passwords for each account help mitigate this threat.
Brute Force Attacks:
In a brute-force attack, hackers try many combinations to guess a password. Longer, complex passwords and additional authentication methods reduce vulnerability to such attacks.
Man-in-the-Middle Attacks (MITM):
In MITM attacks, attackers intercept data as it travels over networks. Avoid using public Wi-Fi for sensitive activities, or use a VPN to ensure a secure connection.
5. Password Hygiene Tips
Sign Out of Shared Devices:
If you access accounts on shared or public devices, always sign out afterward to prevent unauthorized access.
Monitor Accounts Regularly:
Regularly review accounts for suspicious activity. Detecting and addressing unauthorized activity quickly can prevent further damage.
Secure Account Recovery Options:
Review and secure account recovery methods, such as security questions and backup email accounts. Choose recovery answers that are not easily guessable or publicly available.
6. Should You Use Biometrics or Passwordless Options?
Many platforms now offer biometric or passwordless login options, which can be more convenient and secure than traditional passwords.
Biometric Authentication:
Biometric logins, such as fingerprints or facial recognition, add convenience without compromising security. These options are harder to replicate and can reduce reliance on passwords.
Passwordless Login:
Passwordless methods use unique, time-sensitive codes sent to a device or email. These are secure options for protecting sensitive accounts, though they still often require additional steps, such as a backup password or security question.
Conclusion: Strengthening Password Security for a Safer Digital Experience
Creating strong, unique passwords and managing them properly is foundational for protecting your digital life. By following these best practices—creating complex, unique passwords, using a password manager, enabling two-factor authentication, and staying vigilant about cybersecurity threats—you can significantly enhance your security. In a world where cyber threats are constantly evolving, robust password practices are your first line of defense.
Invest in your security by making these practices a habit, and enjoy the peace of mind that comes with knowing your information is protected.

