How can I create an effective incident response plan for cyber incidents?
In today’s digital environment, cyber incidents are an inevitable risk for organizations of all sizes. An effective incident response plan (IRP) helps mitigate the damage, streamline recovery, and minimize financial and reputational impact. Crafting a well-prepared IRP ensures your business is ready to respond swiftly, systematically, and effectively. This guide covers the essential steps in building a robust cyber incident response plan.
What is an Incident Response Plan (IRP)?
An incident response plan is a documented, systematic approach that defines how a business detects, responds to, and recovers from cyber incidents. These incidents range from minor security breaches to large-scale cyberattacks, including malware infections, ransomware attacks, and data breaches.
A successful IRP involves pre-defined actions and guidelines that help the incident response team (IRT) contain the threat, restore systems, and reduce the chance of similar incidents in the future.
The Importance of an Incident Response Plan
Without an IRP, organizations often experience delays and confusion in addressing cyber incidents, which can exacerbate the damage. An effective IRP allows for a faster, coordinated response, reducing the risk of prolonged downtime, data loss, and financial costs. Additionally, having a tested and efficient response plan can improve client confidence and compliance with regulatory requirements.
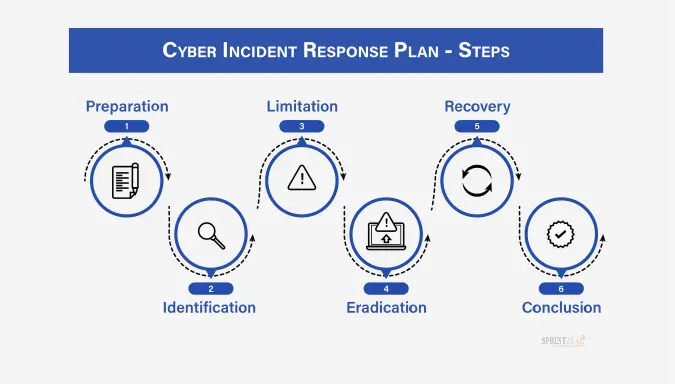
Key Steps to Develop an Effective Incident Response Plan
1. Establish an Incident Response Team (IRT)
Assemble a dedicated team of individuals responsible for executing the IRP. This team should include representatives from various departments, such as IT, legal, communications, and executive leadership, to ensure a coordinated response across the organization.
Key IRT Roles:
- Incident Response Manager: Leads the team, coordinating efforts and communicating with executives.
- IT and Security Team Members: Responsible for identifying, analyzing, and mitigating threats.
- Legal Advisor: Provides guidance on regulatory requirements and legal considerations.
- Communications Specialist: Manages communication with employees, clients, and media if necessary.
2. Define and Classify Potential Incidents
Identifying different types of cyber incidents and classifying them by severity helps prioritize response efforts. Each type of incident may require a unique approach, so it’s essential to define them within the plan.
Common Cyber Incident Types:
- Malware Attacks: Unauthorized software disrupts systems or steals data.
- Phishing Attacks: Attackers attempt to acquire sensitive information via deceptive emails.
- Data Breaches: Unauthorized access results in compromised sensitive data.
- Denial of Service (DoS) Attacks: Cybercriminals overload systems to disrupt services.
Create incident severity levels (e.g., low, medium, high, critical) to help the team determine the response needed for each category.
3. Establish Detection and Reporting Protocols
Early detection is essential for minimizing the impact of an incident. Set up processes to monitor for unusual activities, such as sudden spikes in network traffic or unauthorized logins. Detection tools like intrusion detection systems (IDS) and endpoint detection and response (EDR) solutions help identify threats in real-time.
Develop a clear reporting protocol to ensure that anyone who suspects or identifies an incident can quickly notify the IRT. This protocol should outline how incidents are reported, including contact information, reporting templates, and escalation processes.
4. Outline Incident Containment and Mitigation Steps
Containment and mitigation are critical for preventing the spread of an incident and minimizing damage. Your plan should include immediate steps to isolate affected systems, prevent unauthorized access, and contain the incident.
Key Containment Tactics:
- Short-Term Containment: Implement immediate actions, like disconnecting compromised systems from the network, to prevent further spread.
- Long-Term Containment: Develop strategies for ensuring that the threat does not reoccur, such as applying patches or strengthening access controls.
Once containment measures are in place, begin mitigation efforts to resolve the root cause of the incident and prevent future occurrences.
5. Develop a Recovery Plan
A recovery plan guides the IRT in restoring systems and returning to normal operations. This phase involves verifying the integrity of restored systems, reinstalling applications, and ensuring that all patches and updates are in place to prevent repeat incidents.
Recovery Considerations:
- Data Restoration: Use clean backups to restore data, ensuring no remnants of the incident remain.
- System Validation: Conduct tests to verify that systems are functioning correctly before bringing them back online.
- User Access Restoration: Gradually restore access, starting with essential personnel and gradually including others.
6. Create a Communication Strategy
Effective communication is essential throughout the incident response process. Clear communication ensures that stakeholders, including employees, clients, and regulatory bodies, understand the situation and the steps being taken to resolve it.
Your IRP should define communication protocols for:
- Internal Communication: Keep employees informed about their roles and responsibilities.
- External Communication: Communicate transparently with clients and stakeholders to maintain trust.
- Media and Public Relations: If necessary, provide accurate and timely updates to the media to control the narrative.
7. Conduct a Post-Incident Analysis and Review
A post-incident analysis is critical for learning from the incident and enhancing your IRP. This review should evaluate what worked well and what could be improved, providing an opportunity to refine your incident response processes.
Post-Incident Analysis Steps:
- Incident Summary: Document key details, including the type of attack, affected systems, and timelines.
- Response Evaluation: Analyze the effectiveness of the response, including response time, communication, and containment.
- Improvement Recommendations: Identify lessons learned and update the IRP to address any identified weaknesses.
8. Regularly Update and Test the Incident Response Plan
Cyber threats are constantly evolving, so it’s essential to keep your IRP up to date. Regularly reviewing and testing the plan, at least annually, helps ensure it remains effective. Conducting drills and tabletop exercises allows your team to practice and refine their response techniques.
Benefits of a Well-Prepared Incident Response Plan
Creating a robust incident response plan offers several advantages for your business:
- Reduced Downtime: An efficient IRP minimizes system downtime, allowing faster recovery.
- Minimized Financial Losses: By containing incidents quickly, your business can avoid costly data breaches and regulatory fines.
- Enhanced Customer Confidence: A transparent and effective response plan helps maintain client trust and business reputation.
- Improved Compliance: Many regulations require businesses to have a documented incident response plan.
Conclusion
Building an effective incident response plan is essential for minimizing the impact of cyber incidents on your business. By assembling a capable IRT, defining clear response protocols, and conducting regular reviews, you can stay prepared for potential cyber threats. A comprehensive, proactive approach to incident response not only protects your business but also strengthens its resilience in an increasingly digital world.

