What should I include in a cybersecurity policy for my employees?
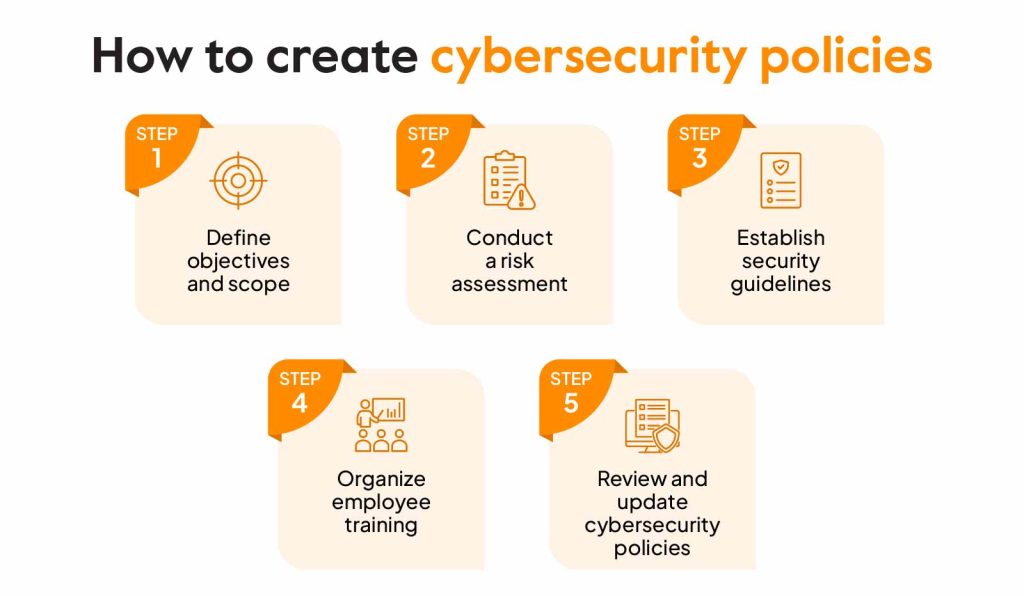
In today’s digital age, establishing a robust cybersecurity policy is crucial for any organization. Such a policy not only protects sensitive information but also cultivates a culture of security awareness among employees. Here’s a detailed look at what to include in a comprehensive cybersecurity policy for your business.
1. Purpose of the Policy
Begin your policy by clearly outlining its purpose. Explain the importance of cybersecurity in protecting the organization’s assets and data. This section sets the tone for the policy and highlights the organization’s commitment to security.
2. Scope of the Policy
Define who the policy applies to. This includes all employees, contractors, and third-party vendors who access company resources. Clarifying the scope ensures everyone understands their responsibilities regarding cybersecurity.
3. Acceptable Use Policy
Outline what constitutes acceptable and unacceptable use of company resources, including:
- Internet browsing
- Email communications
- Personal device usage
- Software installations
By establishing clear guidelines, you can minimize the risk of security breaches.
4. Password Management
Password security is fundamental to cybersecurity. Include guidelines for creating strong passwords, changing them regularly, and using password managers. You might also want to mandate multi-factor authentication (MFA) for an extra layer of security.
5. Data Protection and Handling
Detail how employees should handle sensitive information. Include instructions on:
- Classifying data based on sensitivity
- Encrypting data in transit and at rest
- Proper disposal of sensitive information
This section is vital for ensuring compliance with data protection regulations.
6. Incident Response Plan
Outline the steps employees should take in the event of a security incident. This includes:
- Reporting incidents immediately
- Identifying the type of incident (e.g., phishing, data breach)
- Understanding escalation procedures
Having a well-defined response plan can significantly reduce the impact of an incident.
7. Remote Work Guidelines
With remote work becoming more prevalent, it’s essential to establish security protocols for remote employees. Address issues such as:
- Secure Wi-Fi connections
- Use of VPNs
- Securing home networks and devices
This ensures that employees working remotely maintain security standards comparable to those in the office.
8. Security Awareness Training
Implementing regular security training sessions is crucial for keeping employees informed about the latest threats and best practices. Topics should include:
- Recognizing phishing attempts
- Social engineering tactics
- Safe internet browsing practices
Regular training helps foster a culture of security within the organization.
9. Monitoring and Enforcement
Clarify how compliance with the policy will be monitored and the consequences of policy violations. This may include periodic audits, software monitoring, and disciplinary actions for non-compliance.
10. Review and Updates
Cybersecurity is an ever-evolving field, and policies should be reviewed and updated regularly. Specify a timeline for policy reviews and identify who is responsible for maintaining the policy.
Conclusion
Creating a robust cybersecurity policy is an essential step in safeguarding your organization against cyber threats. By incorporating these elements, you can ensure that employees understand their roles in maintaining a secure work environment. Regular training and updates will help keep your policy relevant and effective.

